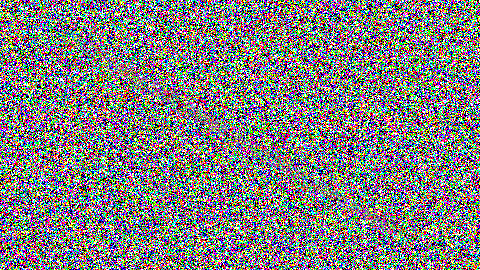In this challenge by CyberSpace we were given a picture named enc.png and the python source code which was used to add shapes or used make the picture pixelated, the encoded picture looked like this.
The python code which was provided and the one which was used to encode this was this :
1 | import numpy as np |
At first what i thought was it was steganography so, i tried to use tools for that but it didn’t worked so, what i did was read the code and get to know it was encoded by that code.
Then after, i thought it was supposed to meet the seed value for decoding but i wasn’t.
To decode i make our favorite ChatGpt and it gave me the code to reverse it which was this.
1 | import cv2 |
and then used this code in the same directory where the enc.png was and it gave me the decoded image file named flag.png.
flag: CSCTF{why_SKK_image_encryption_sooo.weak}